Breaking Data Silos: Path to Strategic Success
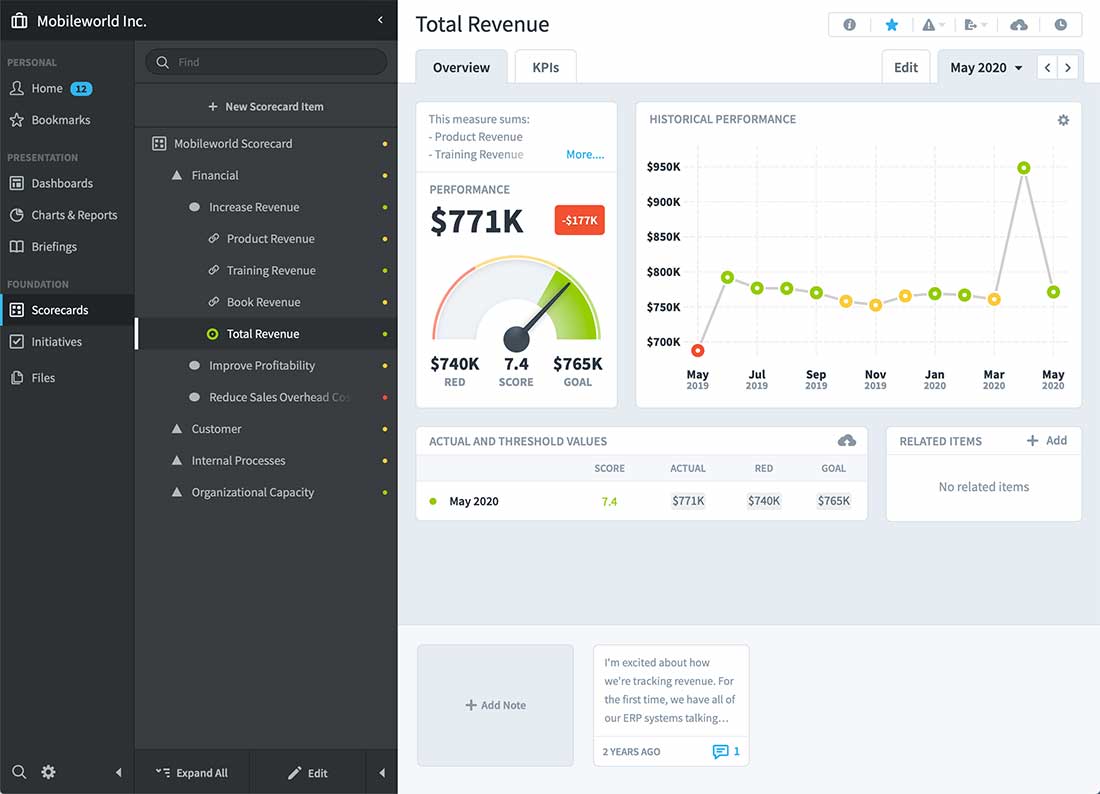
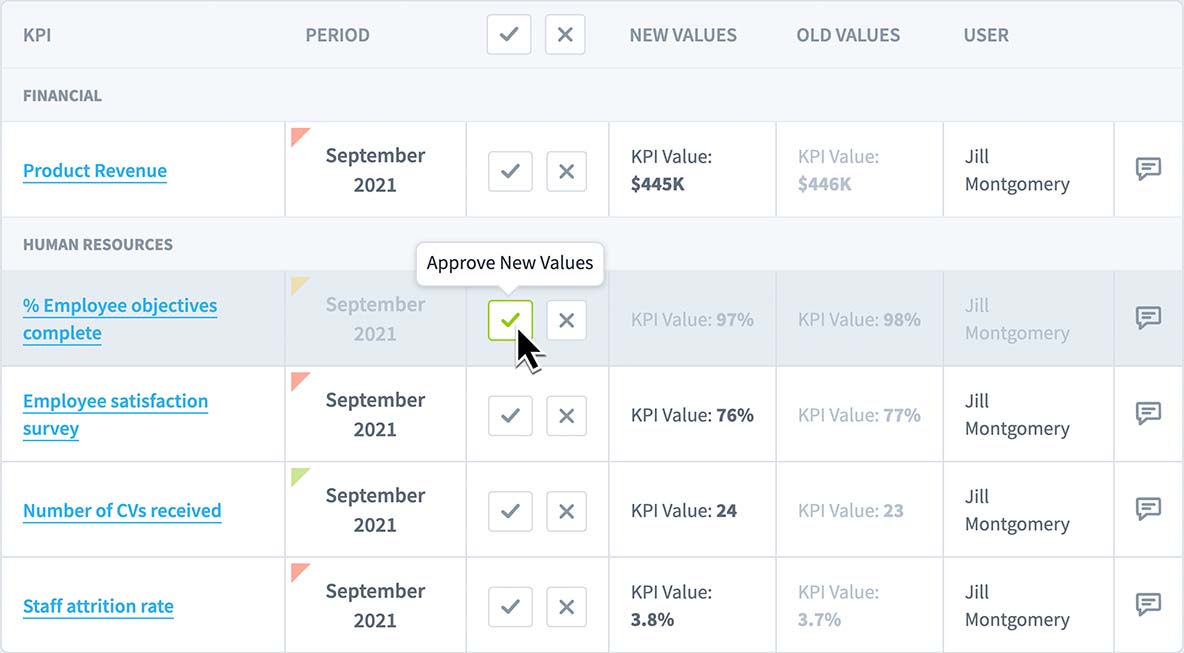
Data silos hinder strategic alignment, causing departments to work toward disconnected goals. This guide explores how centralized data management breaks down these silos, enabling unified decision-making, improved efficiency, and proactive strategy adjustments.